Ransomware – The do’s and don’ts to protect you and your business
 Ransomware (viral infections that encrypt data on your hard drive), are becoming more prevalent. Cryptowall and Cryptolocker are two that are increasingly infecting computers world wide, with an estimated 545,000 infections from between Sep 2013 to May 2014. Ransomwares’ purpose is to attempt to extort money from the victim with the promise that your data will be restored after payment.
Ransomware (viral infections that encrypt data on your hard drive), are becoming more prevalent. Cryptowall and Cryptolocker are two that are increasingly infecting computers world wide, with an estimated 545,000 infections from between Sep 2013 to May 2014. Ransomwares’ purpose is to attempt to extort money from the victim with the promise that your data will be restored after payment.
The Senior Manager of Symantec’s Cyber Readiness & Response, Bob Shaker recently stated, “We’ve seen a sharp rise in requests from customers with respect to Ransomware.”
Mr Shaker tells the story of trying to help a customer who, after being infected with a ransomware virus, could only sit and watch while his company’s data was wiped out, file by file. “I never want to have to go through that again,” he says.
Since then, Symantec has gone to great efforts to ensure that businesses understand the risks and have a clear picture of what to do, and what not to do, to protect themselves from becoming a victim of Ransomware.
Here are some Ransomware Do’s and Don’ts
1. NEVER pay the Ransom!
Your first response will undoubtedly be panic, and your first instinct will be to pay the Ransom.
Don’t do it. This will just encourage the attackers, and help fund further development of these types of attacks.
And even if you do pay, there is no guarantee that you will get your data back.
Instead, Do:
Remove the infected system from the network if you are on one, and clean the system of all viruses.
Then restore data from a known good backup. Restoring data from a backup is the quickest way to get back up and running.
2. Do install a quality security solution
A multi-faceted security solution (like Norton Internet Security for example) should be installed. Norton has protections for not just file-based threats (traditional Viruses), but it also includes download protection, browser protection, heuristic detection technologies, a firewall and a community sourced file reputation scoring system.
3. Do educate employees
One of the main ways you can be infected is through “Spear Phishing”. This is whereby an unsolicited email arrives from an unknown sender that incorporates an attachment that, when opened, executes a program (the virus).
If you have employees, you must take the time to educate them about these threats, and how to recognise suspicious links and attachments, and what they should do in such circumstances.
4. Do use content scanning and filtering on your mail servers
All Incoming emails should be scanned for known threats and should block any attachment types that could potentially pose a threat.
5. Do make sure that all computers and software are kept up-to-date with security patches and updates
Compromised websites are frequently used to spread viruses. Regular patching of vulnerable software like Internet Browsers, Java, and Adobe Flash is necessary to help prevent infection.
6. Do limit end user access to mapped network drives
Ransomware is capable of looking for and encrypting data on any mapped drives that a user has access to. Restricting permissions for shared folders and files of a mapped network drive will limit what the Ransomware virus will be able to encrypt.
7. Do make sure that you have a comprehensive backup solution in place.
The fastest way to get back up and running after this sort of attack is to have a backup of your data.
These Dos and Don’ts will not prevent an attack, but they can certainly reduce your risk level.




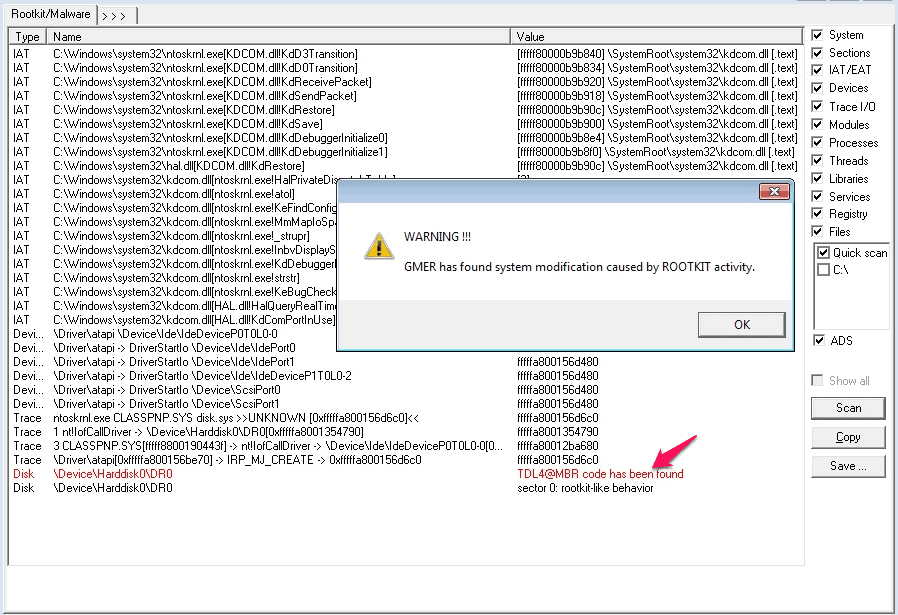
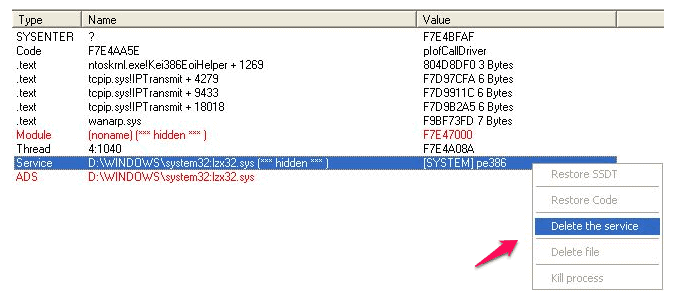
 I recently had a Laptop in the workshop that had a particularly difficult to remove Rootkit Virus installed on it.
I recently had a Laptop in the workshop that had a particularly difficult to remove Rootkit Virus installed on it.