Top 5 Reasons to Use WordPress
This article pretty well sums up all the reasons why WordPress is my choice of platform for a CMS (Content Management System) website.
Article by Khaled Shihabi
Individuals who are just starting out in the world of Internet marketing might find that it is somewhat overwhelming at first. There are so many different choices they need to make and if they are not careful they can end up spending weeks or even months reading and learning without taking any action. The most important step toward success in Internet marketing is taking that first step. The first thing people can do is deciding what type of content management system (CMS) they will use. A CMS is a system that allows users to manage a wide variety of content in an easy to use way.
The vast majority of sites on the Internet today use some sort of content management system because they are so simple to set up and extremely customizable. The most popular options are WordPress, Movable Type, Drupal, Custom CMS and Blogger/Blog Spot. Each of these tools has its own set of loyal users, but most people agree that WordPress is the ideal option for almost any type of site. People just starting out who haven’t yet made a dime, and people who have been doing it for years earning millions of dollars use it.
The top 5 reasons to use WordPress are:
1. WordPress is free to use – WordPress is an open source piece of software that is completely free to use. Many of the other options may be free for a limited time, or free to use with limited features but not completely free. WordPress, on the other hand, is free to use forever, and there are no restrictions on the features you can use or how many sites you can use it on.
2. Finding WordPress hosting is extremely easy – Creating a website with WordPress is so easy because almost all web hosting companies support the technologies needed to run WordPress. In fact, many companies have specific WordPress hosting options available that will allow the WordPress software to be installed automatically with just one click. This means it is possible to have a site up and running within minutes of signing up for some hosting packages.
3. There are thousands of WordPress plugins – A plugin is a small piece of software written to expand the features of another piece of software. WordPress is an open source content management system, which means that other programmers can see its code and write plugins to help make WordPress look and function exactly as they want it to. Thousands of these plugins are available for free so website owners can create a truly unique sites that have all the amazing features available on the web today.
4. Google loves WordPress – Anyone looking to make money on the Internet will quickly learn that one of the best ways to get visitors to their site is through Google. The WordPress system is designed with Google’s search algorithms in mind. In addition, many of the plugins are written specifically to optimize a site for Google. This gives site owners who use the WordPress content management system a big leg up over their competition. It makes running a site much easier and less time consuming than could otherwise be possible.
5. WordPress is expandable – When people start out with their first website they often don’t fully grasp how big it could become. As time goes by site owners will continue to add more and more content, and without a good content management system it will quickly become confusing and difficult to browse for the users. In addition, the technologies used on these sites continue to advance as more and more features are being developed. Using WordPress allows the web master to keep everything well organized, and the software is updated regularly to ensure all the latest technologies can be used seamlessly on any site.
Article Source: EzineArticles.com




 Could your computer or networking equipment be one of more than 10,000 that are still affected by the “DNSChanger” malware from last year?
Could your computer or networking equipment be one of more than 10,000 that are still affected by the “DNSChanger” malware from last year?
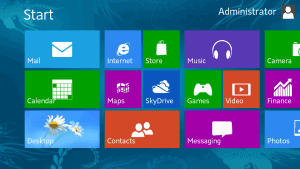 A beginners guide to Microsoft’s soon to be released Operating System Windows 8.
A beginners guide to Microsoft’s soon to be released Operating System Windows 8.







 Up until about 2012, I was of the opinion that AVG Free was as good as any Antivirus software, on the proviso that you didn’t do stupid things online like visiting porn websites, clicking on links in emails that were obvious phishing scams and making sure you kept Windows up to date along with Java, Adobe Flash and Adobe Reader.
Up until about 2012, I was of the opinion that AVG Free was as good as any Antivirus software, on the proviso that you didn’t do stupid things online like visiting porn websites, clicking on links in emails that were obvious phishing scams and making sure you kept Windows up to date along with Java, Adobe Flash and Adobe Reader.

