 Well I’ve come to the conclusion that if people want a safer Internet browsing experience, then everyone needs to critically look at what they are doing online, how they are doing it, and what they should be doing but aren’t.
Well I’ve come to the conclusion that if people want a safer Internet browsing experience, then everyone needs to critically look at what they are doing online, how they are doing it, and what they should be doing but aren’t.
It has become painfully evident that the main reason PC’s are getting infected and compromised with viruses and malware is because of the User’s activities online, in conjunction with the User’s reluctance to do updates when they are presented. The reason why updates are important to safe browsing is because if you don’t do them, simply visiting a compromised or deliberately malicious website can infect your PC. This is regardless of what Security software you use. There are something like 50,000 new viruses being released every single day, so it is near on impossible to protect yourself against that.
The other subject I will cover is what Browser I recommend and why, but I’ll address the updates issue first.
I am consistently told by User’s that they do not do updates for several reasons. Those being:
- I never know if they are legitimate.
- They take too long.
- I have done updates in the past and they caused problems.
- I couldn’t be bothered.
Let’s look at these excuses one by one.
I never know if they are legitimate. This is just a ridiculous thing to say. If you get a pop-up or a message that tells you there is an update available, and you don’t know whether it is legitimate, then you must also believe that you are infected with something malicious, so why aren’t you doing something about it? You must do all updates including Java, Adobe Flash, Adobe Reader, and all Windows Updates. These updates generally address security holes that can be exploited by Hackers and bad people in general. It is a no brainer and is not an option.
They take too long. Seriously? You can sit on Facebook for two hours but you don’t have time to do updates? Try this. Switch on the computer, let it boot-up, get your updates underway and go for a walk in the fresh air. Both yourself and your computer will be better for it.
I have done updates in the past and they caused problems. This one I can understand. I’ve done plenty of updates myself and afterwards the computer has crashed or something else just isn’t right. However, this just isn’t an excuse for not doing updates. There will be some underlying problem that has caused the issue. You might already be infected with a virus that is screwing up the update for example. Whatever the issue, you should address it and resolve it.
I couldn’t be bothered. Well what can I say to this? If this is your attitude then expect that it will be a case of when you get infected rather than if. Not much more to say about this one!!!
Also, when you are thinking updates, DON’T FORGET to make sure you always have the latest version of your Security Software and Browser.
For example, quite often I see people with AVG 2011 or 2012 installed, but the current version is 2013.
The same applies to your Browser.
I see Internet Explorer 8 installed, when IE9 (latest version compatible with XP) or IE10 is available.
What Browser should you use?
I think the Browser of choice is Mozilla Firefox.
My reasons for thinking this are:
- It’s more secure than the default Internet Explorer.
- You can install add-on’s and extensions that give it greater functionality, but more importantly extra security.
Which Add-on’s or Extensions should you use in Firefox?
Well there are literally thousands of Add-on’s and Extensions available, but there are 3 that I consider essential.
They are:
- NoScript – No longer available.
- BetterPrivacy – No longer available.
- Adblock Plus – This Add-on isn’t specifically a security Add-on, but by blocking Ad’s, you won’t be tempted to click on things you possibly shouldn’t. Besides, who needs all those Ad’s anyway? Adblock Plus blocks all annoying ads on the web by default: video ads on YouTube, Facebook ads, flashy banners, pop-ups, pop-unders and much more.
What about Security Software?
My advice to people on this changes periodically.
13 years ago I would have recommended VET Antivirus, but then it changed to CA Antivirus and that’s when the problems started. Since then the recommendations have ranged from a choice of free to paid for products.
Currently I am recommending Norton Internet Security.
I am finding that this product is offering very good protection, functions and features including Social Media protection, and at a price of $29 for 12 months cover, it’s great value as well.
So what does it all mean?
The main points are:
- Do all the updates including Windows, Java, Adobe Flash and Adobe Reader.
- Use Firefox with the recommended Extensions and Add-on’s.
- Use good security software.
But above all else, use your brain before clicking on or downloading anything.
Be absolutely sure that you know it is legitimate first.
Spotty Dog Computer Services can help provide you with a Safer Internet Browsing experience.



 I recently read a quote that was meant to apply to Businesses, but equally applies to anyone online. And it went like this:
I recently read a quote that was meant to apply to Businesses, but equally applies to anyone online. And it went like this:
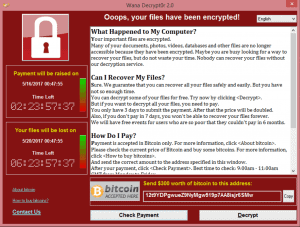
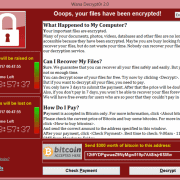
 Ransomware has been on the rise over the last six months.
Ransomware has been on the rise over the last six months.


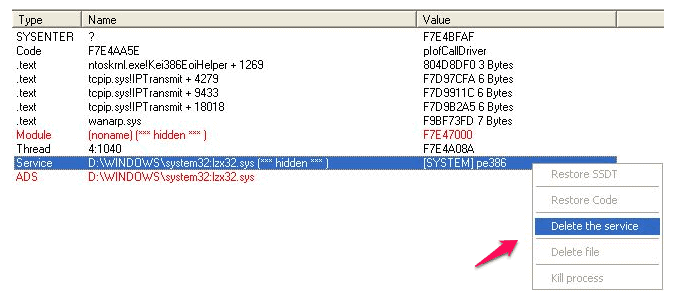
 I recently had a Laptop in the workshop that had a particularly difficult to remove Rootkit Virus installed on it.
I recently had a Laptop in the workshop that had a particularly difficult to remove Rootkit Virus installed on it.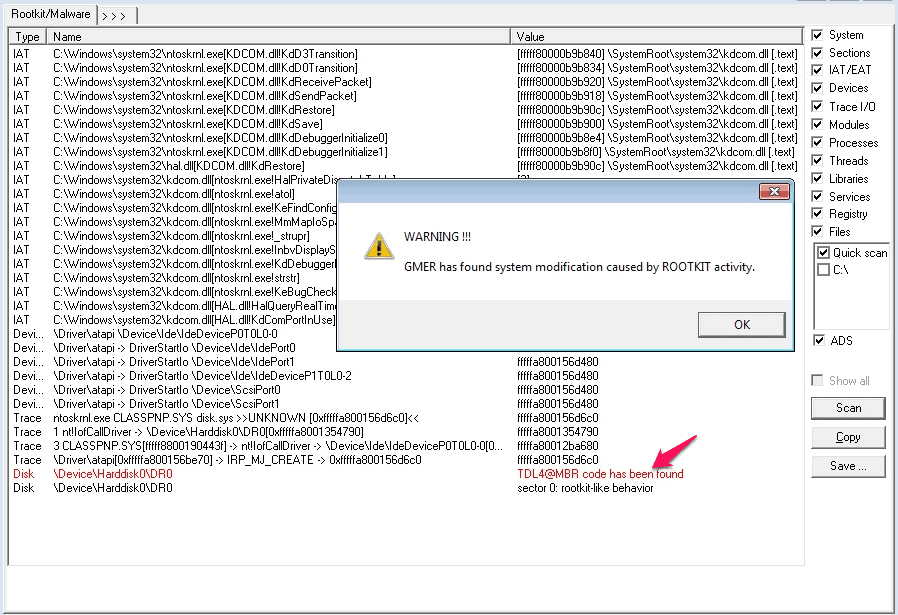



 Increasingly I am seeing not only my own business targeted, but I am getting a huge amount of inquiries from other businesses asking me if something they received in an email or through the post or via the telephone is legitimate or a scam.
Increasingly I am seeing not only my own business targeted, but I am getting a huge amount of inquiries from other businesses asking me if something they received in an email or through the post or via the telephone is legitimate or a scam.
 Well I’ve come to the conclusion that if people want a safer Internet browsing experience, then everyone needs to critically look at what they are doing online, how they are doing it, and what they should be doing but aren’t.
Well I’ve come to the conclusion that if people want a safer Internet browsing experience, then everyone needs to critically look at what they are doing online, how they are doing it, and what they should be doing but aren’t.
 Adobe has released a critical update to users of their Reader software, patching a critical vulnerability that can allow hackers to take control of a victims’ computer.
Adobe has released a critical update to users of their Reader software, patching a critical vulnerability that can allow hackers to take control of a victims’ computer.
 Could your computer or networking equipment be one of more than 10,000 that are still affected by the “DNSChanger” malware from last year?
Could your computer or networking equipment be one of more than 10,000 that are still affected by the “DNSChanger” malware from last year?